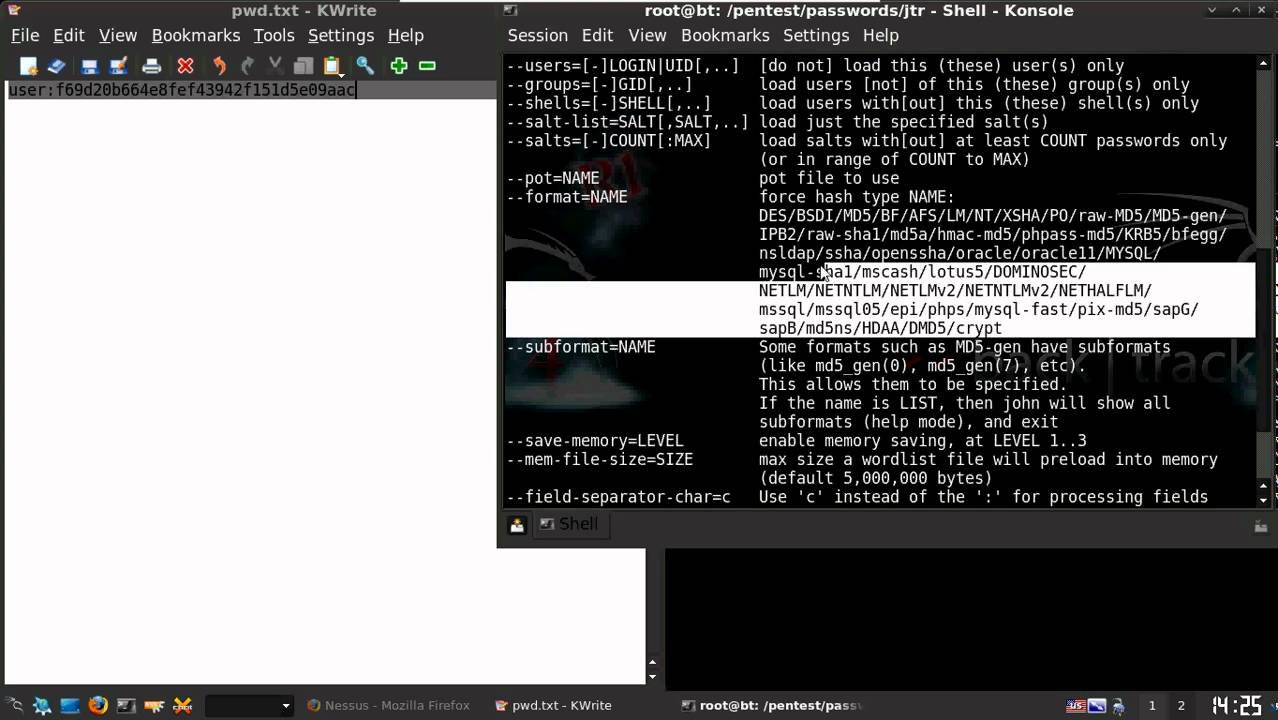
If you run john again, you will get: john hash.txt Using default input encoding: UTF- 8 Loaded 1 password hash (PKZIP 32 / 64 ) No password hashes left to crack (see FAQ) This means that the password has already been ripped, to print password check.john/john.pot file or use -show option. $./john -show././encrypted.hash 0 password hashes cracked, 1 left Still does not crack password but at least it did not core dump and it actually says 0 cracked, 1 left 👍 This comment has been minimized. Nov 10, 2015 Cracking password using John the Ripper. In Linux, password hash is stored in /etc/shadow file. For the sake of this exercise, I will create a new user names john and assign a simple password ‘password’ to him. I will also add john to sudo group, assign /bin/bash as his shell.
- John The Ripper 0 Password Hashes 1 Left Hand Piano
- John The Ripper 0 Password Hashes 1 Left Hand Thread
- John The Ripper 0 Password Hashes 1 Left Hand
|
John the Ripper's cracking modes.
Mode descriptions here are short and only cover the basic things.Check other documentation files for information on customizing themodes.
Wordlist mode.
This is the simplest cracking mode supported by John. All you need todo is specify a wordlist (a text file containing one word per line)and some password files. You can enable word mangling rules (whichare used to modify or 'mangle' words producing other likelypasswords). If enabled, all of the rules will be applied to everyline in the wordlist file producing multiple candidate passwords fromeach source word.
The wordlist should not contain duplicate lines. John does not sortentries in the wordlist since that would consume a lot of resourcesand would prevent you from making John try the candidate passwords inthe order that you define (with more likely candidate passwords listedfirst). However, if you don't list your candidate passwords in areasonable order, it'd be better if you sort the wordlistalphabetically: with some hash types, John runs a bit faster if eachcandidate password it tries only differs from the previous one by afew characters. Most wordlists that you may find on the Net arealready sorted anyway.
On the other hand, if your wordlist is sorted alphabetically, you donot need to bother about some wordlist entries being longer than themaximum supported password length for the hash type you're cracking.To give an example, for traditional DES-based crypt(3) hashes onlythe first 8 characters of passwords are significant. This means thatif there are two or more candidate passwords in the wordlist whosefirst 8 characters are exactly the same, they're effectively the same8 character long candidate password which only needs to be tried once.As long as the wordlist is sorted alphabetically, John is smart enoughto handle this special case right.
In fact, it is recommended that you do not truncate candidatepasswords in your wordlist file since the rest of the characters(beyond the length limit of your target hash type) are likely stillneeded and make a difference if you enable word mangling rules.
The recommended way to sort a wordlist for use with default wordlistrule set is:
See RULES for information on writing your own wordlist rules.
'Single crack' mode.
John The Ripper 0 Password Hashes 1 Left Hand Piano
This is the mode you should start cracking with. It will use thelogin names, 'GECOS' / 'Full Name' fields, and users' home directorynames as candidate passwords, also with a large set of mangling rulesapplied. Since the information is only used against passwords for theaccounts it was taken from (and against password hashes which happenedto be assigned the same salt), 'single crack' mode is much faster thanwordlist mode. This permits for the use of a much larger set of wordmangling rules with 'single crack', and their use is always enabledwith this mode. Successfully guessed passwords are also tried againstall loaded password hashes just in case more users have the samepassword.
Note that running this mode on many password files simultaneously maysometimes get more passwords cracked than it would if you ran it onthe individual password files separately.

'Incremental' mode.
This is the most powerful cracking mode, it can try all possiblecharacter combinations as passwords. However, it is assumed thatcracking with this mode will never terminate because of the number ofcombinations being too large (actually, it will terminate if you set alow password length limit or make it use a small charset), and you'llhave to interrupt it earlier.
That's one reason why this mode deals with trigraph frequencies,separately for each character position and for each password length,to crack as many passwords as possible within a limited time.
To use the mode you need a specific definition for the mode'sparameters, including password length limits and the charset to use.These parameters are defined in the configuration file sections called[Incremental:MODE], where MODE is any name that you assign to the mode(it's the name that you will need to specify on John's command line).You can either use a pre-defined incremental mode definition or define acustom one.
As of version 1.8.0, pre-defined incremental modes are 'ASCII' (all 95printable ASCII characters), 'LM_ASCII' (for use on LM hashes), 'Alnum'(all 62 alphanumeric characters), 'Alpha' (all 52 letters), 'LowerNum'(lowercase letters plus digits, for 36 total), 'UpperNum' (uppercaseletters plus digits, for 36 total), 'LowerSpace' (lowercase letters plusspace, for 27 total), 'Lower' (lowercase letters), 'Upper' (uppercaseletters), and 'Digits' (digits only). The supplied .chr files includedata for lengths up to 13 for all of these modes except for 'LM_ASCII'(where password portions input to the LM hash halves are assumed to betruncated at length 7) and 'Digits' (where the supplied .chr file andpre-defined incremental mode work for lengths up to 20). Some of themany .chr files needed by these pre-defined incremental modes might notbe bundled with every version of John the Ripper, being available as aseparate download.
See CONFIG and EXAMPLES for information on defining custom modes.
External mode.
You can define an external cracking mode for use with John. This isdone with the configuration file sections called [List.External:MODE],where MODE is any name that you assign to the mode. The sectionshould contain program code of some functions that John will use togenerate the candidate passwords it tries. The functions are coded ina subset of C and are compiled by John at startup when you request theparticular external mode on John's command line. See EXTERNAL.
John The Ripper 0 Password Hashes 1 Left Hand Thread
What modes should I use?
See EXAMPLES for a reasonable order of cracking modes to use.
John The Ripper 0 Password Hashes 1 Left Hand
$Owl: Owl/packages/john/john/doc/MODES,v 1.6 2013/05/29 17:57:56 solar Exp $