
- چگونه نشت DNS را رفع کنیم؟. راه حل این است که مطمئن شوید هنگامی که به VPN متصل هستید، تنها از DNS سرور این شبکه ناشناسی استفاده میکنید. در OpenVPN نسخه 2.3.9 و به بعد با اضافه کردن یک گزینه میتوانید.
- A lot of them are DNSSEC capable and use strong encryption as-is. This, coupled with no logging and a VPN connection are essential in the modern world. deleted 4 years ago. Disable DHCP, setup a static IP and change your DNS to Google DNS. 8.8.8.8 and 8.8.4.4.
How to check and fix a DNS leak
I already touched base on this under post “How to make VPNs more secure”, here is a even more detailed and separate explanation. When using an anonymity or privacy service, it is extremely important that all traffic originating from your computer is routed through the anonymity network. If any traffic leaks via the underlying connection, any entity monitoring your traffic will be able to log your activity.
DNS or the domain name system is used to translate domain names such as www.privacyinternational.org into numerical IP addresses e.g. 123.123.123.123 which are required to route packets of data on the Internet. Whenever your computer needs to contact a server on the Internet, such as when you enter a URL into your browser, your computer contacts a DNS server and requests the IP address. Most Internet service providers assign their customers a DNS server which they control and use for logging and recording your Internet activities.
Under certain conditions, even when connected to the anonymity network, the operating system will continue to use its default DNS servers instead of the anonymous DNS servers assigned to your computer by the anonymity network. DNS leaks are a major privacy threat since the anonymity network may be providing a false sense of security while private data is leaking.
If you are concerned about DNS leaks, you should also understand transparent DNS proxy technology to ensure that the solution you choose will stop the DNS leak.
Public DNS Server Tool is a small utility for changing the DNS servers in Windows XP, Vista and 7 on the fly.I have seen that recently many public DNS servers have been made available for everyone's use.
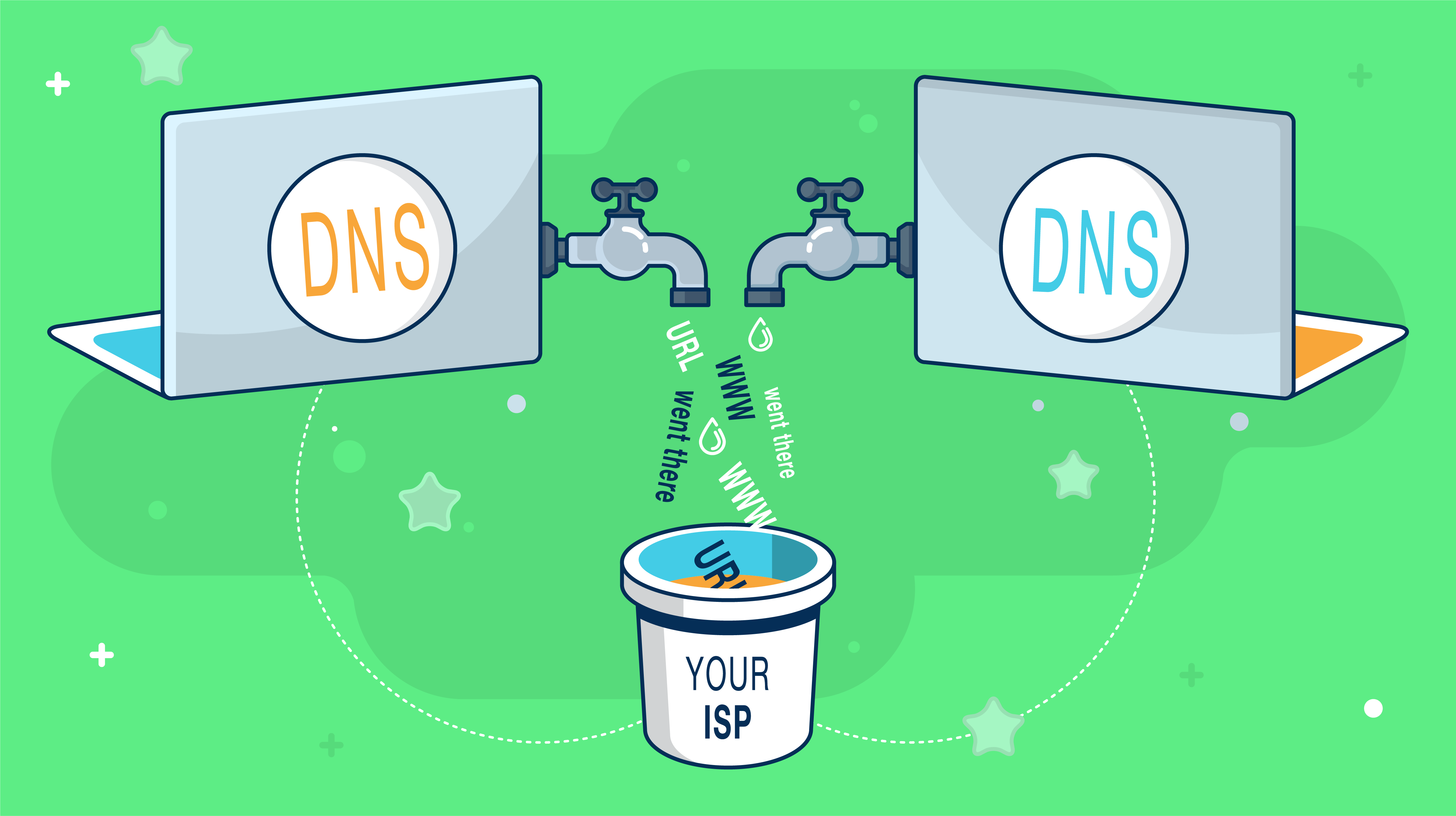
Some ISP’s are now using a technology called ‘Transparent DNS proxy’. Using this technology, they will intercept all DNS lookup requests (TCP/UDP port 53) and transparently proxy the results. This effectively forces you to use their DNS service for all DNS lookups.
If you have changed your DNS settings to an open DNS service such as Google, Comodo or OpenDNS expecting that your DNS traffic is no longer being sent to your ISP’s DNS server, you may be surprised to find out that they are using transparent DNS proxying.
However, the greatest threat is if you choose to use an open DNS service to protect your privacy if your VPN service leaks dns requests. This would give you a false sense of security whilst you are connected to the VPN while your DNS requests are intercepted by your ISP.
When using a VPN service one might expect that all of the user’s traffic will go through the privacy network, but on rare occasions a phenomenon known as “DNS leakage” might occur. This means that rather than using the DNS servers provided by the VPN operator, it’s possible that the user’s default DNS servers will be used instead or otherwise become visible
A DNS leak may happen whenever a DNS query ‘bypasses’ the routing table and gateway pushed by the OpenVPN server. The trigger on Windows systems may be as simple as a slight delay in the answer from the VPN DNS, or the VPN DNS unable to resolve some name.
How to fix a DNS leak:
The solution is to ensure that once connected to the anonymity network, you are using ONLY the DNS server/s provided by the anonymity service. As this problem affects predominantly windows clients, only solutions for Windows appear here.
3 basic steps to fix the problem;
- Before connecting to the VPN, set static IP address properties if you are using DHCP
- After connecting, remove DNS settings for the primary interface
- After disconnecting, switch back to DHCP if neccessary or reapply original static DNS servers
Solution A (Automatic)
If you are using OpenVPN on Windows XP/Vista/7 then a fully automated solution is available.
Download dnsfixsetup.exe
(md5 checksum: f212a015a890bd2dae67bc8f8aa8bfd9)
After installation, when you connect to a VPN server, a batch file will be run executing the 3 steps above.
Three scripts are generated for each OpenVPN configuration file;
- configfilename_pre.bat - executed before the connection is established - Calls pre.vbs - If any active DHCP adapters exist, switch to static
- configfilename_up.bat - executed when the connection is established - Calls up.vbs - Clear the DNS servers for all active adapter except the TAP32 adapter
- configfilename_down.bat - executed after the connection is disconnected - Calls down.vbs - Reconfigure adapters back to their original configuration
Dnsfixsetup Exe Editor
Solution B (Manually clearing the DNS)
- Open the command prompt (cmd.exe) as an administrator.
- Before connecting identify the name of the connected network interface. In the case below it is “Local Area Connection”
netsh interface show interface
- Connect to the VPN. Once connected proceed to the next step.
- Flush the DNS resolver cache
ipconfig /flushdns
Disable the DNS configuration for the Interface identified in step 1
netsh interface IPv4 set dnsserver “Local Area Connection” static 0.0.0.0
both
- Test for DNS leaks.
- After disconnecting, reconfigure the adapter to renew the previous DNS settings

netsh interface IPv4 set dnsserver “Local Area Connection” dhcp
Dnsfixsetup Exe Online
Once again, flush the DNS resolver cache.
ipconfig /flushdns
Done.