To use RSA with Mbed TLS or any other application, you will most likely need an RSA key pair. An RSA key pair is often stored in either a PEM file or a DER file.
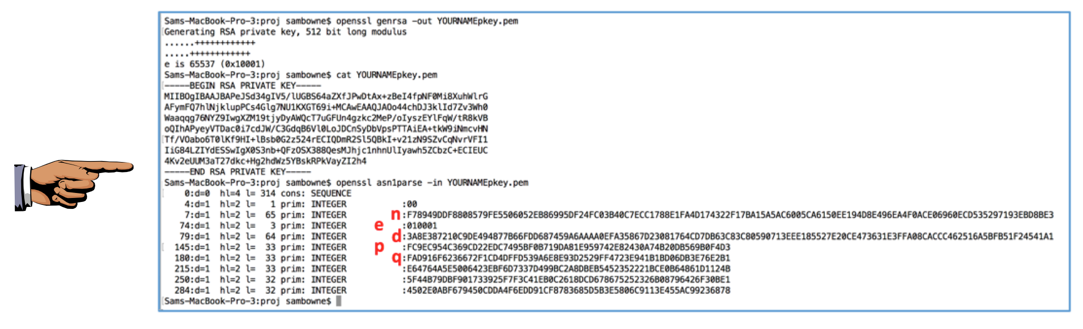
You want to use RSA to encrypt data, and you need to generate a public key and its corresponding private key. Use a cryptography library's built-in functionality to generate an RSA key pair. Here we'll describe the OpenSSL API. If you insist on implementing RSA yourself (generally a bad idea), see the following discussion. After you've checked for existing SSH keys, you can generate a new SSH key to use for authentication, then add it to the ssh-agent. To generate an RSA key pair and create a certificate with the public key. Openssl pkcs12 -in c. In order to generate an RSA key, an EVPPKEY must first be allocated with EVPPKEYnew: An exponent for the key is also needed, which will require allocating a BIGNUM with BNnew and then assigning with BNsetword: To generate the key, create a new RSA with RSAnew and call RSAgeneratekeyex: RSA.rsa; rsa = RSAnew ; RSAgeneratekeyex. Generating an RSA Private Key Using OpenSSL. You can generate an RSA private key using the following command: openssl genrsa -out private-key.pem 3072. In this example, I have used a key length of 3072 bits. While 2048 is the minimum key length supported by specifications such as JOSE, it is recommended that you use 3072.
Building the RSA key pair generator
Mbed TLS ships with the source code for an RSA key pair generator application, called gen_key. To build the executable for the application, please check out the building Mbed TLS.
After the compilation, the executable is often located in programs/pkey/gen_key.
The gen_key application has the following arguments and options:
Generating an RSA key pair
To actually generate an RSA key pair, you have to decide which size your RSA key should be. Depending on your need for security, we advise you to use at least 2048 bits, and use 4096 bits or higher if you have very high security requirements.
To use the RSA key pair generator to generate a 4096 bits RSA key and save that key in PEM format in private.key, use:
The larger the requested keysize, the longer it will take to generate the key itself. You also need to take into account the performance of the system.
The key generator also outputs the key in human readable format in addition to writing the key to the requested keyfile in the requested format.
The output for a 1024-bit RSA key looks something like this:
Did this help?
Для начала подробнее о версии ПО:
ciscoasa# sh ver
Cisco Adaptive Security Appliance Software Version 8.6(1)2
Device Manager Version 6.6(1)
Compiled on Fri 01-Jun-12 02:16 by builders
System image file is 'disk0:/asa861-2-smp-k8.bin'
Config file at boot was 'startup-config'
Licensed features for this platform:
-------------
VPN-3DES-AES : Disabled perpetual
-------------
Лицензия на стойкое шифрование отсутствует.
Настройка удаленного доступа к устройству
Telnet
ciscoasa(config-if)# nameif Mgmt
INFO: Security level for 'Mgmt' set to 0 by default.
ciscoasa(config-if)# security-level 100
ciscoasa(config-if)# ip address 10.0.0.2 255.255.255.0
ciscoasa(config-if)# no shut
ciscoasa(config-if)# exit
ciscoasa(config)# exit
ciscoasa# write memory
ciscoasa(config)# telnet ?
configure mode commands/options:
Hostname or A.B.C.D The IP address of the host and/or network authorized to
login to the system
X:X:X:X::X/<0-128> IPv6 address/prefix authorized to login to the system
timeout Configure telnet idle timeout
Видно, что можно настроить доступ с определенного IP или имени хоста.
configure mode commands/options:
A.B.C.D The IP netmask to apply to the IP address
ciscoasa(config)# telnet 10.0.0.1 255.255.255.255 ?
configure mode commands/options:
Current available interface(s):
Mgmt Name of interface Management0/0
ciscoasa(config)# exit
passwd 2KFQnbNIdI.2KYOU encrypted
ciscoasa(config)# username mangmt password cisco privilege 15
ciscoasa(config)#aaa authentication telnet consol LOCAL
SSH
Настройка SSH доступа осуществляется достаточно просто и практически аналогична настройке SSH на любом другом устройстве Cisco.ciscoasa(config)#http server enable
http server enable
configure mode commands/options:
certificate-authentication Enable client certificate authentication
client-version The SSL/TLS protocol version to use when acting
as a client
encryption This is the encryption method(s) used with ssl.
The ordering of the algorithms specifies the
preference.
server-version The SSL/TLS protocol version to use when acting
as a server
trust-point Configure the ssl certificate trustpoint
ciscoasa(config)# ssl server-version ?
configure mode commands/options:
any Enter this keyword to accept SSLv2 ClientHellos and either SSLv3
or TLSv1 will be negotiated
sslv3 Enter this keyword to accept SSLv2 ClientHellos and negotiate
SSLv3
sslv3-only Enter this keyword to accept ClientHellos only from a client
using SSLV3
tlsv1 Enter this keyword to accept SSLv2 ClientHellos and negotiate
TLSv1
tlsv1-only Enter this keyword to accept ClientHellos only from a client
using TLSV1
ciscoasa(config)# ssl encryption ?
configure mode commands/options:
3des-sha1 Indicate use of 3des-sha1 for ssl encryption
aes128-sha1 Indicate use of aes128-sha1 for ssl encryption
aes256-sha1 Indicate use of aes256-sha1 for ssl encryption
des-sha1 Indicate use of des-sha1 for ssl encryption
null-sha1 Indicate use of null-sha1 for ssl encryption (NOTE: Data is NOT
encrypted if this cipher is chosen)
rc4-md5 Indicate use of rc4-md5 for ssl encryption
rc4-sha1 Indicate use of rc4-sha1 for ssl encryption
Итак, доступны различные версии SSL/TLS, а так же различные версии шифрования, которые мы можем использовать при подключении к нашему устройству. Попробуем настроить шифрование:
The 3DES/AES algorithms require a VPN-3DES-AES activation key.
Как видно, отсутствие лицензий не дает нам включить стойкое шифрование. Поэтому можем пользоваться только DES.
ciscoasa(config)# ssl encryption des-sha1 null-sha1
ciscoasa(config)# exit
ciscoasa# sh ssl
Accept connections using SSLv2, SSLv3 or TLSv1 and negotiate to SSLv3 or TLSv1
Start connections using SSLv3 and negotiate to SSLv3 or TLSv1
Enabled cipher order: des-sha1 null-sha1
Disabled ciphers: 3des-sha1 rc4-md5 rc4-sha1 aes128-sha1 aes256-sha1
No SSL trust-points configured
Certificate authentication is not enabled
После этого мы можем вводить в строке браузера (Internet Explorer) https://10.0.0.2 и видеть.... что ничего не работает. Не работает оно по следующим причинам: если у нас WinXP, то скорее всего в браузере просто отключена возможность использования SSLv2 и TLSv1. Достаточно зайти в 'Свойства обозревателя', и во вкладке 'Дополнительно' указать нужные галочки:
4. После этого нажимаем 'Применить' и 'ОК' и перезагружаем компьютер (последнее действие выполнять не обязательно, но у меня без перезагрузки не работало).
Не пользуясь оснасткой gpedit аналогичное действие можно сделать путем добавления в реест следующего строкового параметра:
[HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftCryptographyConfigurationSSL00010002]
'Functions'='TLS_RSA_WITH_DES_CBC_SHA,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_RC4_128_SHA,TLS_RSA_WITH_3DES_EDE_CBC_SHA,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P384,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P521,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P384,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P521,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P521,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P384,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P521,TLS_DHE_DSS_WITH_AES_128_CBC_SHA,TLS_DHE_DSS_WITH_AES_256_CBC_SHA,TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA,TLS_RSA_WITH_RC4_128_MD5,SSL_CK_RC4_128_WITH_MD5,SSL_CK_DES_192_EDE3_CBC_WITH_MD5,TLS_RSA_WITH_NULL_MD5,TLS_RSA_WITH_NULL_SHA'
После необходимо настроить Java. Во-первых, если на машине установлено несколько версий, то необходимо включить работу только с одной - 6й. Во-вторых, в Java необходимо разрешить работу с SSLv2.
1. Пуск-Панель управления- Программы-Java. Открываем панель упраления Java, во вкладке Java нажимаем на кнопку View, и выбираем установкой галочек нужную нам версию Java.
Openssl Generate Rsa Key Pair C Example
2. Во вкладке Advanced выбираем поддержку SSLv2.
3. Не забываем в браузере разрешить SSLv2 и TLSv1!
Openssl Generate Rsa Key Pair C
Теперь попытаемся запустить ASDM через Web. Заходим в браузер и в строке адреса вбиваем https://10.0.0.2